The human mind is now a masterpiece of high-level outsourcing. We have willingly, even eagerly, offloaded the most basic data of our own lives to tiny, pocket-shaped silicon brains. We are not forgetful; we are efficiently managed. Consider the phone[…]↓ Read the rest of this entry…
Posts Tagged data
From the outside, an IT department appears to be a group of people who keep the internet from collapsing. But listen to their job titles, and you’d be forgiven for thinking you’ve stumbled into a Renaissance Fair crossed with a[…]↓ Read the rest of this entry…
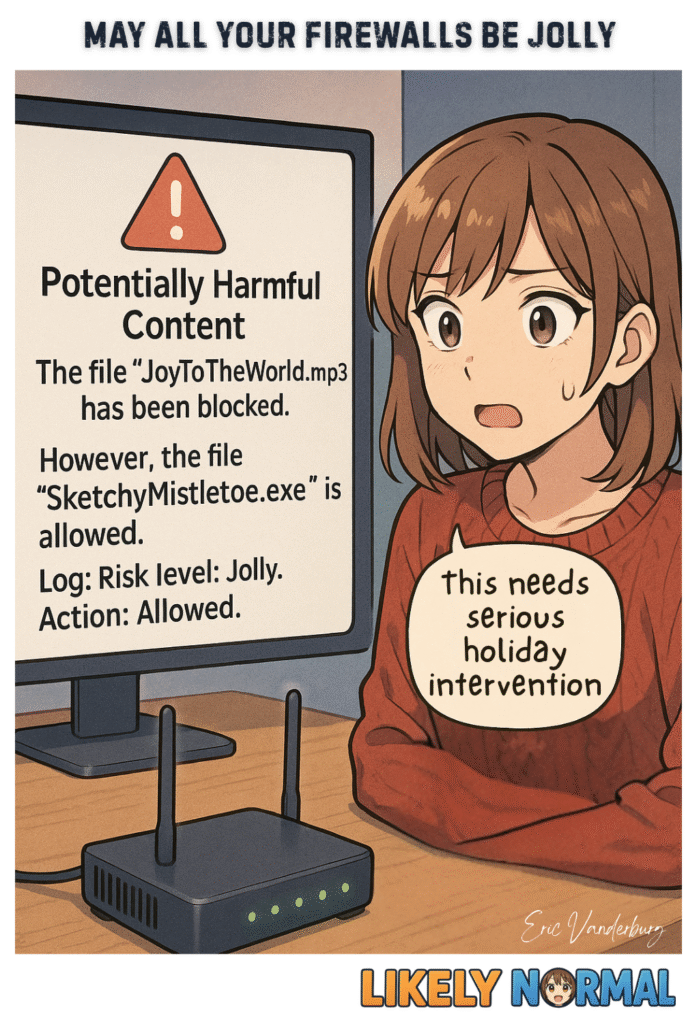
There are some great firewalls out there, but for them to work properly, they must also be configured properly. The problem isn’t firewalls themselves – it’s the half-asleep, checkbox-ticking, “that’s how we’ve always done it” configurations that turn these security[…]↓ Read the rest of this entry…
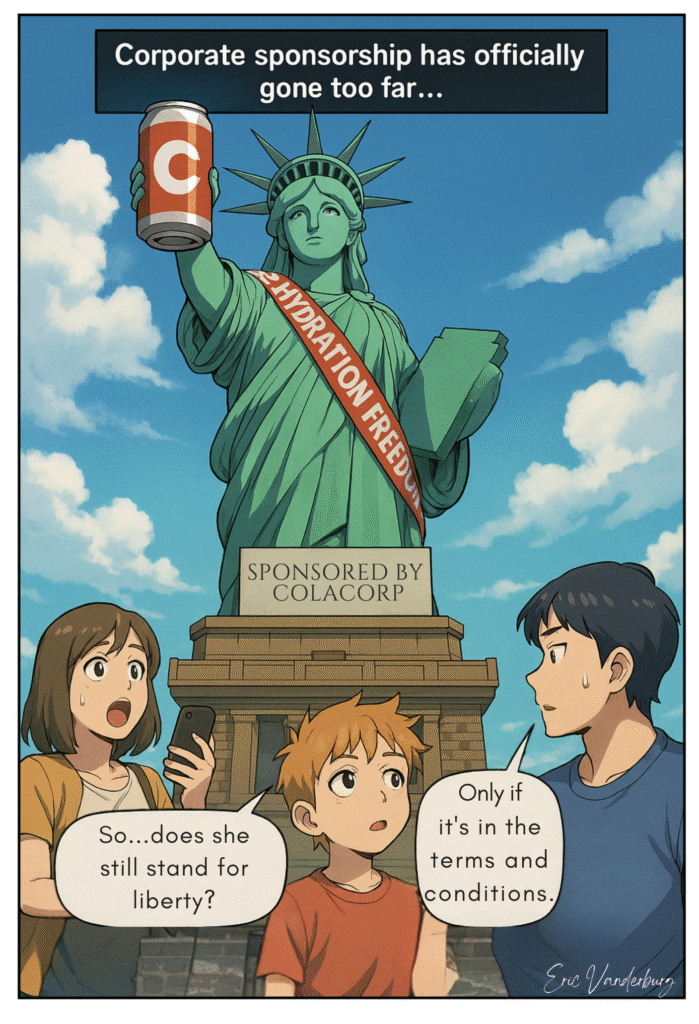
Corporate sponsorship has escaped its natural habitat—the sports field—and now grazes freely across daily life. Once confined to stadium names and NASCAR decals, branding has quietly expanded into schools, parks, museums, and even public bathrooms. This evolution isn’t accidental. Advertising[…]↓ Read the rest of this entry…
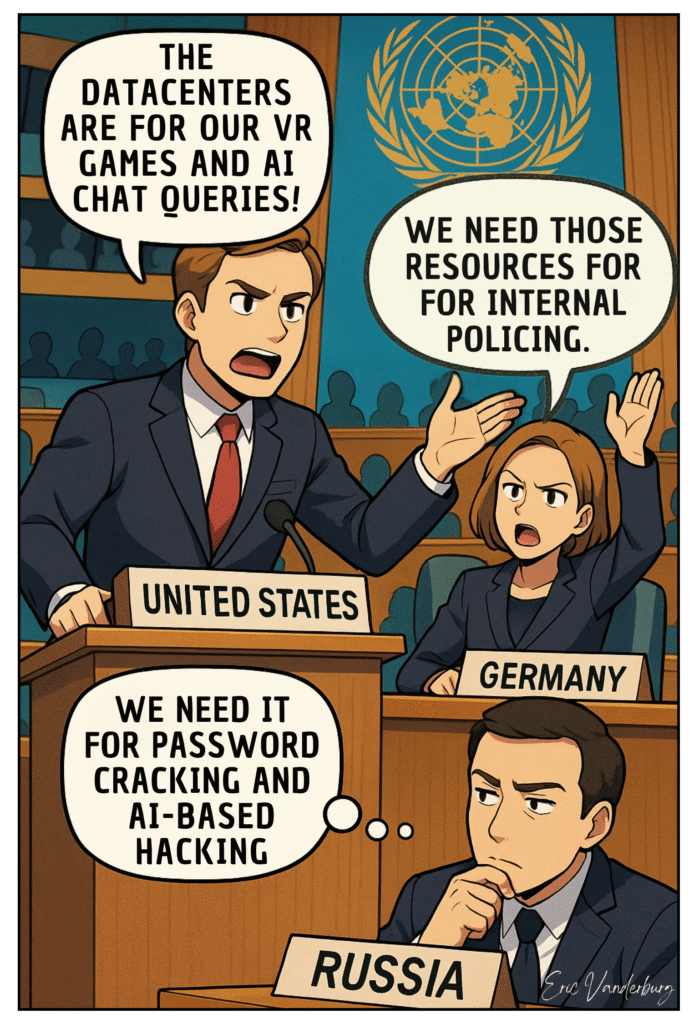
Humanity has a proud and storied tradition of finding things to argue about. For millennia, our battles were fought in Scarcity Mode. We clubbed each other over the last piece of mammoth meat, raised armies over fertile land, and went[…]↓ Read the rest of this entry…
Have you ever encountered that special someone who smiles and nods when tech talk starts, only to reveal they think the cloud is an actual weather phenomenon storing their selfies? These bewildered souls roam among us, living in a delightful[…]↓ Read the rest of this entry…
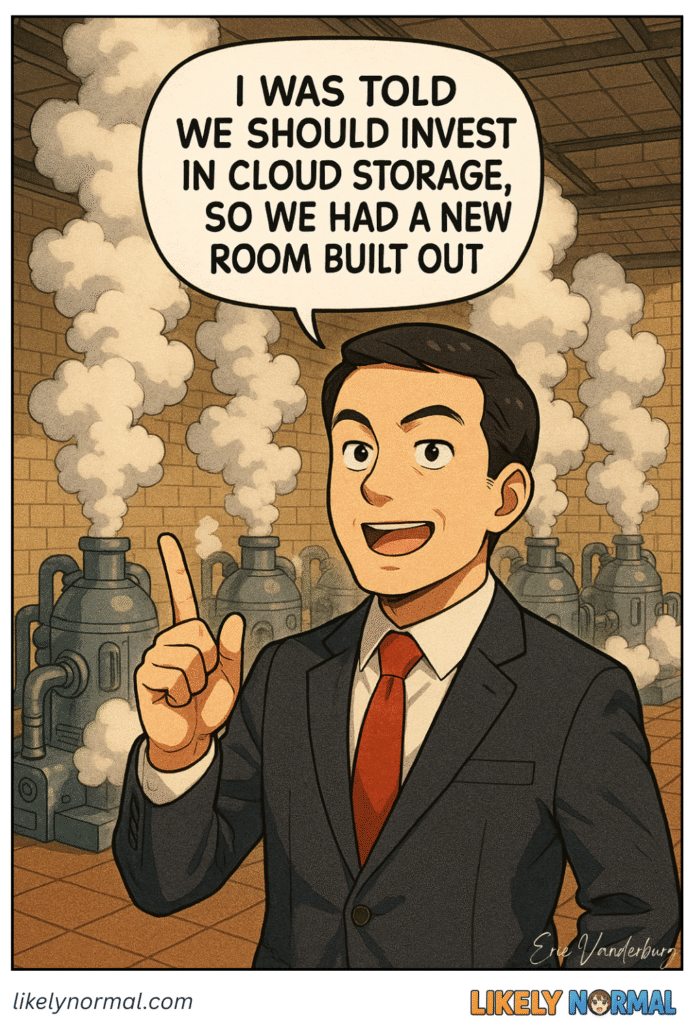
You know those suspiciously cheap cloud services with names like “Elite Secure Cloud Pro” that somehow cost less per year than a Starbucks coffee? These digital snake oil salesmen promise enterprise-grade infrastructure but deliver what feels like a USB stick[…]↓ Read the rest of this entry…
There’s a special kind of genius in the way people—whether employees, students, or children—interpret instructions not as rigid commands, but as loose suggestions open to artistic reinterpretation. It’s not disobedience; it’s innovation. Why solve a problem the boring, intended way[…]↓ Read the rest of this entry…
You bought a VPN because some tech blogger screamed, “public WiFi will get you hacked!” into your eyeballs. And sure, in theory, you’re now a digital ninja, cloaked in encryption, invisible to cybercriminals. But in reality? You’re that person who[…]↓ Read the rest of this entry…
There’s something uniquely demoralizing about being scolded by an algorithm for inactivity while watching a mandatory corporate training video that could put caffeine-fueled squirrels to sleep. You’re just trying to survive another 45-minute lecture on cybersecurity best practices when suddenly—pop-up!—the[…]↓ Read the rest of this entry…