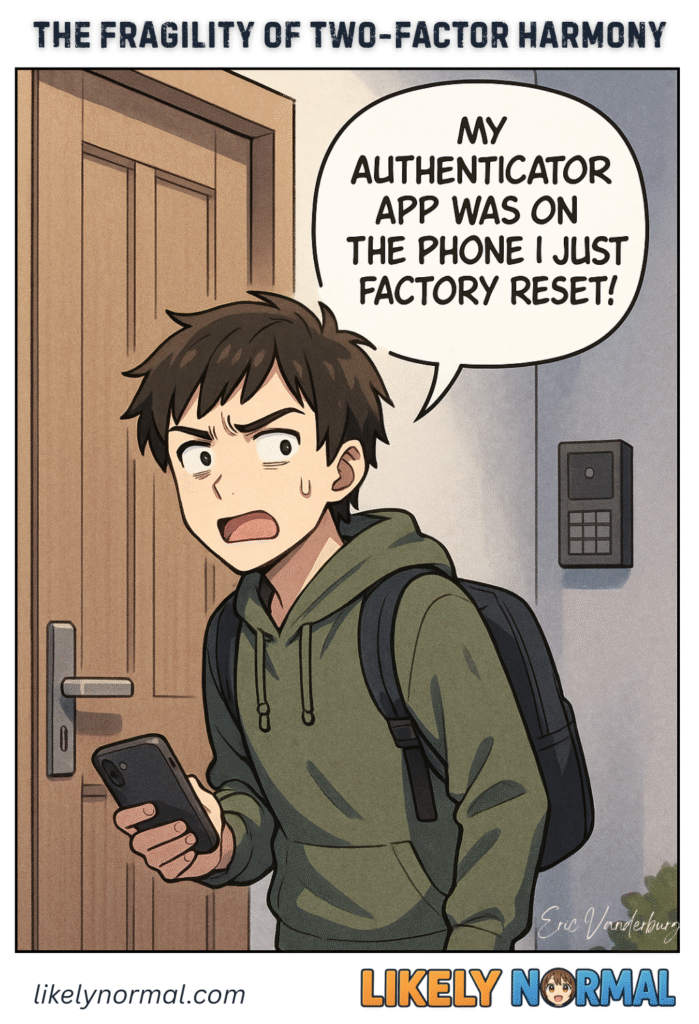
There’s a special kind of modern panic that sets in when you realize you’ve accidentally locked yourself out of your entire digital life. And I owe this particular existential crisis to my shiny new phone—or more accurately, to the 10-minute[…]↓ Read the rest of this entry…
Posts Tagged cybersecurity
There’s a special corporate phenomenon that can sometimes occur in the lead-up to an IPO, acquisition, or any other event where executives want to pretend the company is made of solid gold and good vibes. Suddenly, the very concept of[…]↓ Read the rest of this entry…
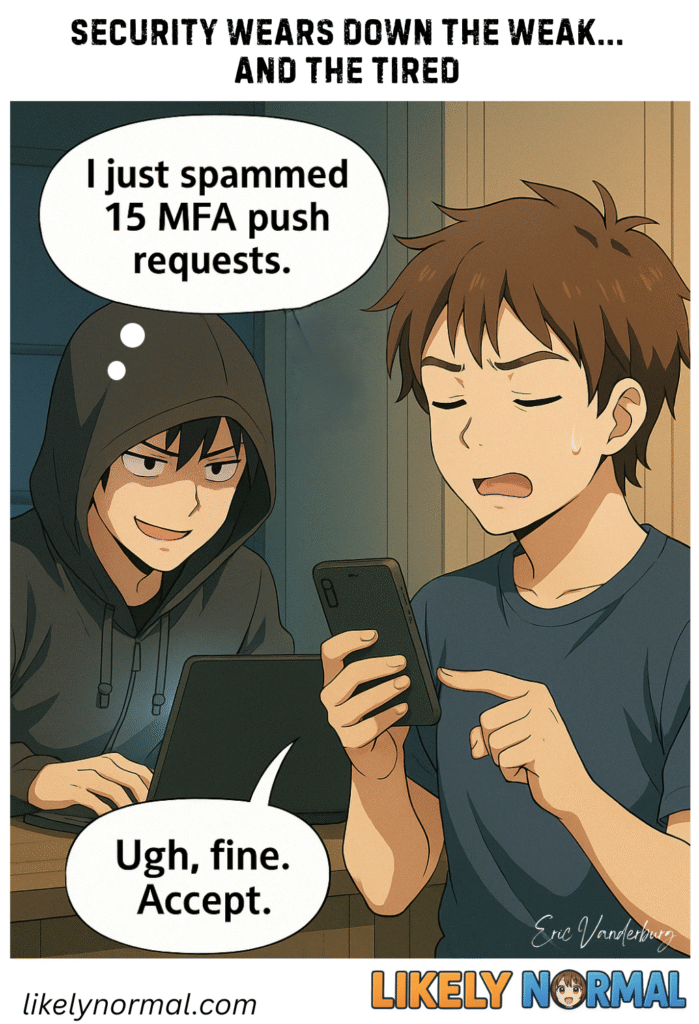
Many people hit that point where cybersecurity feels less like protection and more like a never-ending obstacle course. You’re forced to reset passwords so often you’ve resorted to Password1234_OLD, Password1234_NEW, and Password1234_PLSWORK. Multi-factor authentication now demands your fingerprint, a retinal[…]↓ Read the rest of this entry…
We’ve all sat through the cybersecurity training. We’ve nodded along as IT lectures us about “hovering over links” and “checking sender addresses.” We’ve even scoffed at the hilariously obvious phishing attempts—”URGENT: Your CEO’s Dog Needs Bitcoin!”—feeling smug in our cyber-savviness.[…]↓ Read the rest of this entry…
Datacenters are the beating heart of the digital world—cool, sterile, and filled with the hum of servers doing God’s work. But somewhere between the racks of blinking lights and the guy whose sole job is to “monitor the ping,” you’ll[…]↓ Read the rest of this entry…
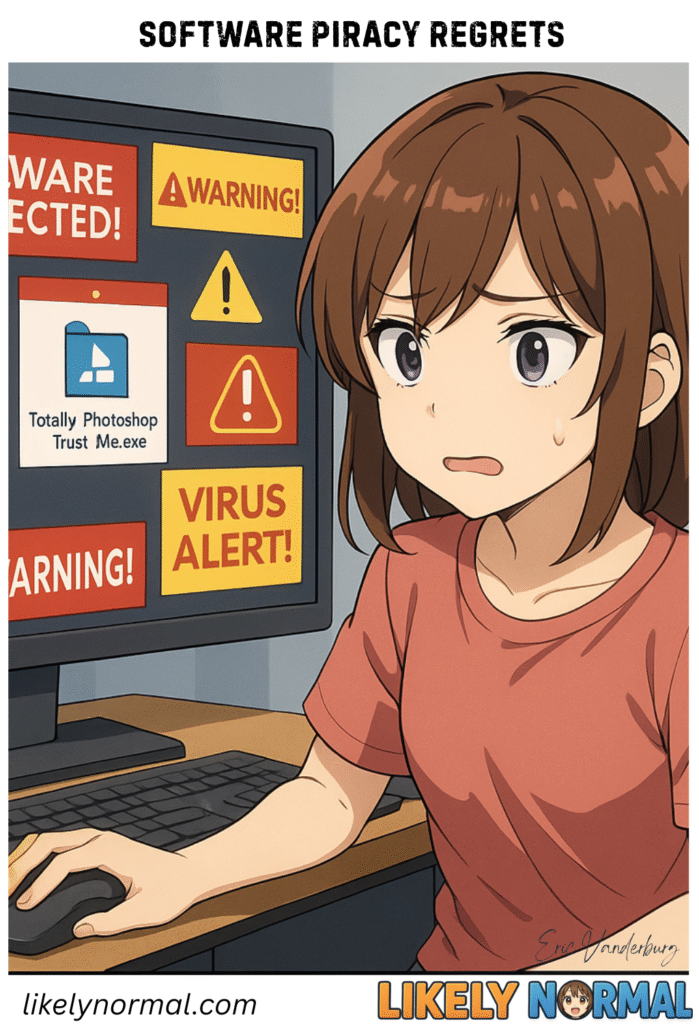
You spot a file named ‘Photoshop_FREE_NoVirus_Promise.exe’ and think, ‘Wow, what a steal! And so legally ambiguous!’ Next thing you know, your computer sounds like a jet engine preparing for takeoff, your files have mysteriously renamed themselves to ‘PLEASE_SEND_BITCOIN.txt,’ and your[…]↓ Read the rest of this entry…